CSCI 2824: Lecture 12
In this lecture, we will present applications of numbers to cryptography and talk about RSA.
Cryptography
What is cryptography? And why is it important?
Crypto: Secret and graphy: writing.
So cryptography is the study of techniques for encrypting and decrypting secrets. With the advent of internet and the need to keep communications across networks secret, cryptography has emerged as an important discipline of computer science and a great application of advanced mathematical techniques to the field.
Example
Imagine Alice and Bob wish to share a secret message between themselves. However, they cannot meet in person in a safe place to do so. Let us suppose the secret message is Party 6:00 p.m, Friday at Zolo's. – Alice.
Let us suppose the secret society (or the government) is quite interested in crashing AliceBob's party. Therefore, it is important for AliceBob to code up their message so that the secret society does not get wind of their party.
Example
In this scenario, let us say that Mr. Ty Coon would like to buy an oil
rig in the middle of campus for 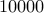 . So he sends a message to the
president of the university:
. So he sends a message to the
president of the university:
Dear President,
I intend to purchase mining rights to the oil reserves underneath your campus for $100000.56 . Students and faculty can be hired to work in this rig for a generous salary of minimum wage.
I remains yours truly,
Mr. Ty Coon
How is the president to know that this important message is from Ty Coon himself as opposed to some student playing a prank? In other words, is there a way that Ty Coon can sign the message so that everyone can authenticate the message as a genuine message from him?
Web
As commerce over www is widespread, people send money over the internet in the form of credit card numbers and payment instructions to banks. Agreements are digitally signed over the network and people log in to secret networks over VPN. All of these nice things are powered by cryptography.
There are two basic types of cryptography:
Private Key Cryptography.
Public Key Cryptography.
Private Key
Private key cryptography consists of encrypting a message 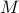 using a secret password
using a secret password 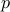 .
Anyone possessing the password can then decrypt the message.
.
Anyone possessing the password can then decrypt the message.
Let us take an example of a very simple and naive private key algorithm using XOR.
XOR
Warning: The XOR scheme here is very easily broken. So do not attempt this.
Let us encode the message into 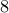 bit chunks (eg., ascii characters).
bit chunks (eg., ascii characters).
Example: Show me da money. The ascii codes are S = 83, h = 104,….
Therefore, the message can be represented as: 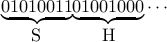 .
.
For simplicity, we can choose the password as a 8 bit string. Example: 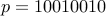
Each 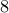 bit ascii character
bit ascii character  is encrypted as:
is encrypted as:
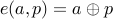
where 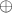 denotes bitwise XOR.
denotes bitwise XOR.
Example: Using password 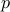 above, the character
above, the character 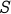 can be encoded as
can be encoded as
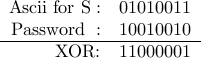
Similarly, other letters can be encoded in the same way.
To decode, we then XOR the encoded message with the same password 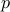 .
.
Example (decryption):

The main property of XOR that is being used here is 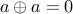 for all
for all  . Therefore
for message
. Therefore
for message 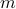 and password
and password 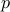 ,
,
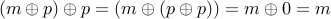
However, XOR is very easy to crack.
Since it translates every character to a different one: Eg., 'S’ (ascii 83) -> ascii 161, it is in effect a transposition cipher. It can be broken by analyzing the relative frequency of coded letters and comparing with frequency in the english language. E is the most commonly used letter, followed by A,O,I, and so on.
Another type of attack is called known plaintext attack. Let us say we know the original message
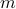 and the encrypted version
and the encrypted version 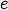 somehow, we can guess the password simply as
somehow, we can guess the password simply as 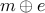 .
.
Therefore, XOR is a naive scheme to use.
DES
DES stands for Data Encryption Standard. It was proposed by IBM researchers in the early 70s with the help of NSA. At a high level, you can think of DES replacing the XOR bitwise operator for a much more complicated looking function. In fact, the function is specified at its core using a lookup tables called S-Boxes. DES uses many tricks to guarantee good security. Yet, it is not unbreakable. For instance, DES uses a 56 bit password (recently upgraded to 64 bits). It can be broken if someone is willing to invest very large amount of computation to brute force the password or use a more intelligent scheme.
Public Key Cryptography
Public key cryptography is very interesting idea that was first invented by British intelligence in the late 60s but kept a secret. It was rediscovered and publicized by Rivest, Shamir and Adelman (RSA) in 1975. Since then it has been a key achievement of number theory in computer science.
Basic idea behind public key cryptography
One can imagine a cryptosystem as a lock that protects a secret. Private key cryptography can be thought of as a traditional lock and key system. The key is the password and if one has the key or can forge one, then one can break into the contents of the box by opening the lock.
Public key cryptosystems are much more interesting. Imagine a lock with two types of keys: a private key that only one person has access to (ideally) and a public key that anyone can obtain. Imagine the lock as operating in one of two ways:
-
If locked with a private key, it can be opened with a public key by anyone.
If locked with a public key, it can be opened by a person with a private key.
How can such a scheme help?
Example
Recall the secret message Alice wishes to send Bob: Party 6:00 p.m, Friday at Zolo's. – Alice. Imagine that every person has a private and a public key to their own box. She can simply take Bob's public key and code up the message and send it to Bob. Since Bob alone has the private key to his box, the message cannot be opened by anyone else.
Example
Suppose Ty Coon writes the letter: Dear President, I intend to purchase mining rights to the oil rig in your campus for $100000.56 . I remains yours truly, Mr. Ty Coon
Is there a way that Ty Coon can sign the message so that everyone can authenticate the message as a genuine message from him? Let us say that TyCoon has a private and a public key. How can TyCoon convince the president of his message's authenticity? Hint Use public/private keys.
RSA
Can we really simulate private/public keys in practice? Yes. This is where number theory comes to the rescue in the form of the RSA crypto system.
Here is the basic idea:
Take two large prime numbers
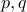 . These have to be large: let us say
. These have to be large: let us say 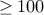 digits.
digits. Compute their product:
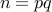 . Also compute
. Also compute 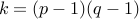 . After that destroy
. After that destroy 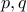 .
.We compute a number
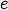 that satisfies:
that satisfies: 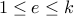 such that
such that 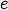 is not a factor of
is not a factor of 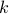 .
.Find numbers
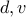 so that
so that 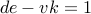 . A fundamental result in number theory says that we can always do so.
. A fundamental result in number theory says that we can always do so.Finally, we keep
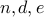 and discard
and discard 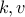 .
. 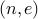 forms the public key and
forms the public key and 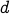 the private key.
the private key.
Let us illustrate this:
Choose
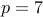 and
and 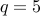 . We have
. We have 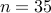 and
and 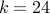 .
.Let us choose
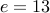 .
.We have to find
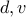 so that
so that 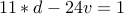 . We have
. We have 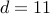 and
and 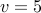 .
.Verify that
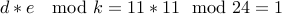 .
.In this case, it is a rather bad coincidence that we have the same public and private key.
The private key is
 . The public key is
. The public key is 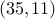 .
.
Encryption: Take a message 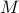 represented as a number from
represented as a number from 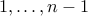 . The encrypted value of
. The encrypted value of 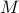 is
is  .
.
Example: Using public key 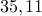 and message
and message 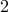 , we have
, we have 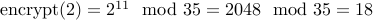 .
.
To decrypt, we have to compute 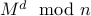 =
= 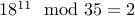 . (Ask google if you do not trust me: [http:www.google.com
. (Ask google if you do not trust me: [http:www.google.com
Breaking RSA
Let us assume that some one has access to the public key 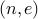 . What stops them from finding out
. What stops them from finding out 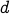 , the secret key?
, the secret key?
After all, 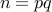 . Therefore, by factorizing
. Therefore, by factorizing 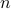 , we can find
, we can find 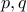 and repeat the process for ourselves to compute
and repeat the process for ourselves to compute 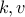 and
and 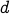 . Once
. Once 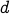 is known then the whole scheme goes kaput.
is known then the whole scheme goes kaput.
Problem (Factoring) Given a number 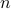 that we are told is the product of two as yet unknown prime numbers
that we are told is the product of two as yet unknown prime numbers 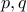 , finding out
, finding out
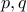 is a hard problem.
is a hard problem.
In order to convince you that factoring a large number say 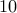 digits is hard, your first programming assignment that will be
out this monday asks you to try and write a factoring routine that given a number
digits is hard, your first programming assignment that will be
out this monday asks you to try and write a factoring routine that given a number 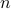 finds a prime factor
finds a prime factor 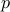 of
of 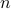 .
You can use any method to do so. However, if you are clever about this, we will have a class competition and your code
may win the competition. :-)
.
You can use any method to do so. However, if you are clever about this, we will have a class competition and your code
may win the competition. :-)
Combinatorially Hard Problems
There are problems in CS which do not have any known algorithms. The class of problems is called NP standing for Non-Deterministic Polynomial Time.
Claim Factoring a number 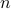 is an example of a hard problem.
is an example of a hard problem.
int factor(int n){ int i; for (i = 0; i < n;++i) if (Divides(i,n)) return i; return NO_FACTOR; }
Time taken to factor by best known algorithm is roughly  .
However, does that preclude a clever and faster algorithm?
.
However, does that preclude a clever and faster algorithm?
The best known factoring algorithm is the general number field sieve. Even though
it is worst case exponential, it has been used to factor large number of upto a 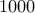 decimal
digits.
decimal
digits.